Among Us Key Algorithm, What Are Common Tasks In Among Us Explained Leveldash Com
Among us key algorithm. Among Us Game lately has been a very by famous games, maybe it is because its extremely funfull game to play. Becoming an impostor are the dream by player in Among us key algorithm game. Because you can kill others and It is funny to watch friends fighting each other to vote for the impostor, and sometimes they are of to fight which player Is the real Impostor Among Us Key Algorithm.
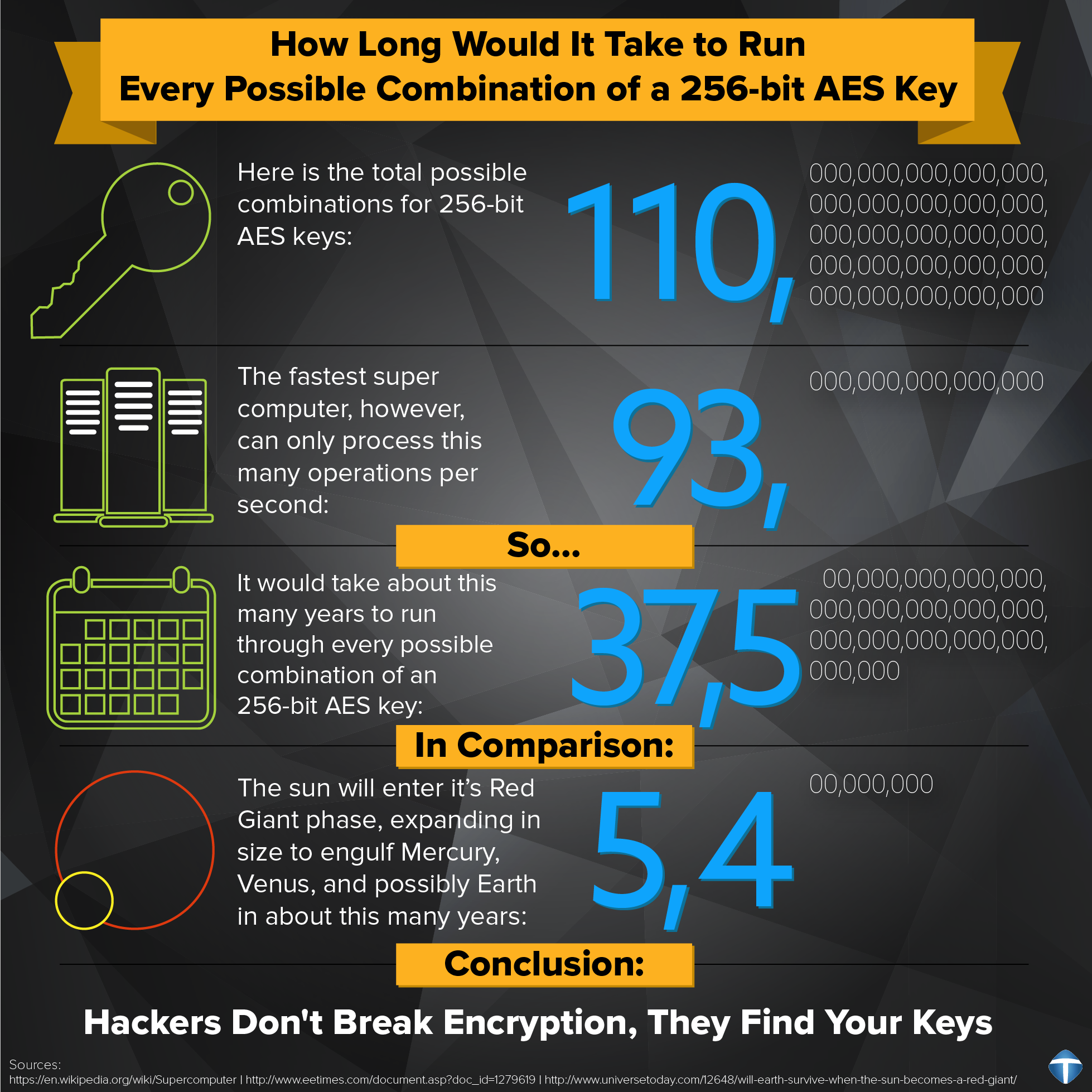
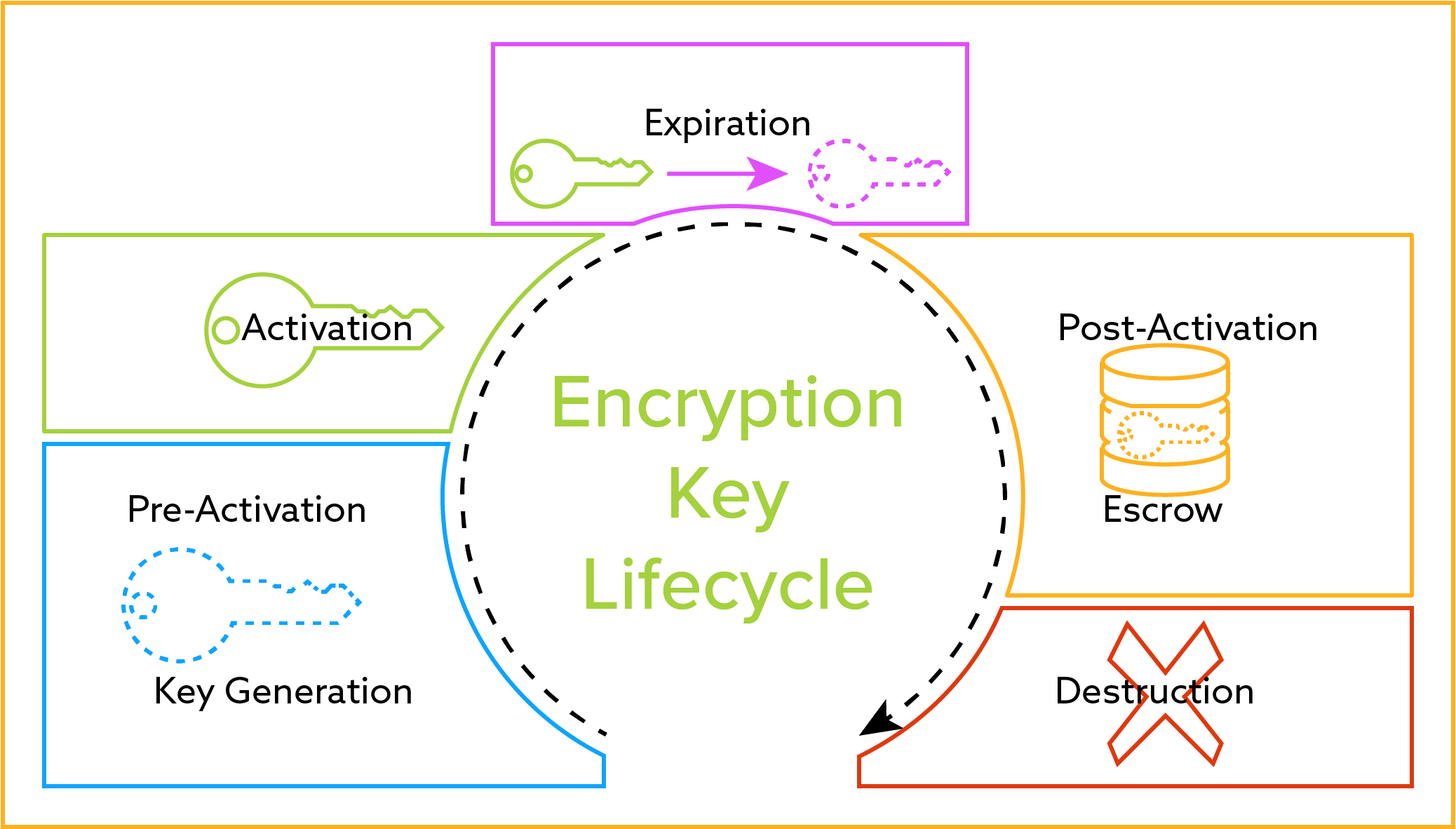
Certain key algorithms when implemented correctly can make a bignum library perform very well.
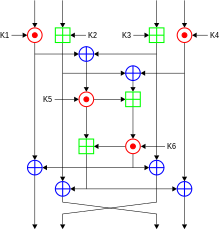
Among us key algorithm. Each one of the sub keys includes 16 bits. How can a computer algorithm specifically learn to take a side or. Multiplication squaring reduction and modular inversion. The key is only restricted by the values indicated in the key usage certificate extension.
The 64 bit input plain text block divided into 4 part 16 bits each declare p1 to p4. This public key is usually referred to as the openpgp key of a person most of the time specified as public openpgp key. This way no one can create license keys unless they have. You might be wondering why are we talking about bias or fairness of algorithms when this is common among humans but not computers.
The best license keys are the ones digitally signed with an asymmetric encryption algorithm. Therefore p1 to p4 will be the inputs for the initial round of the algorithm. This is what you call a key algorithm. Understanding idea algorithm in detail.
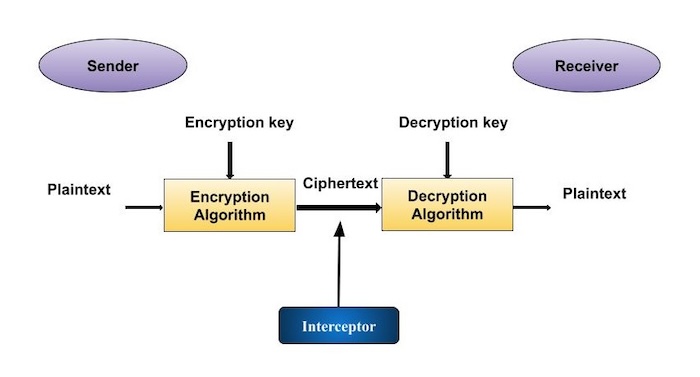
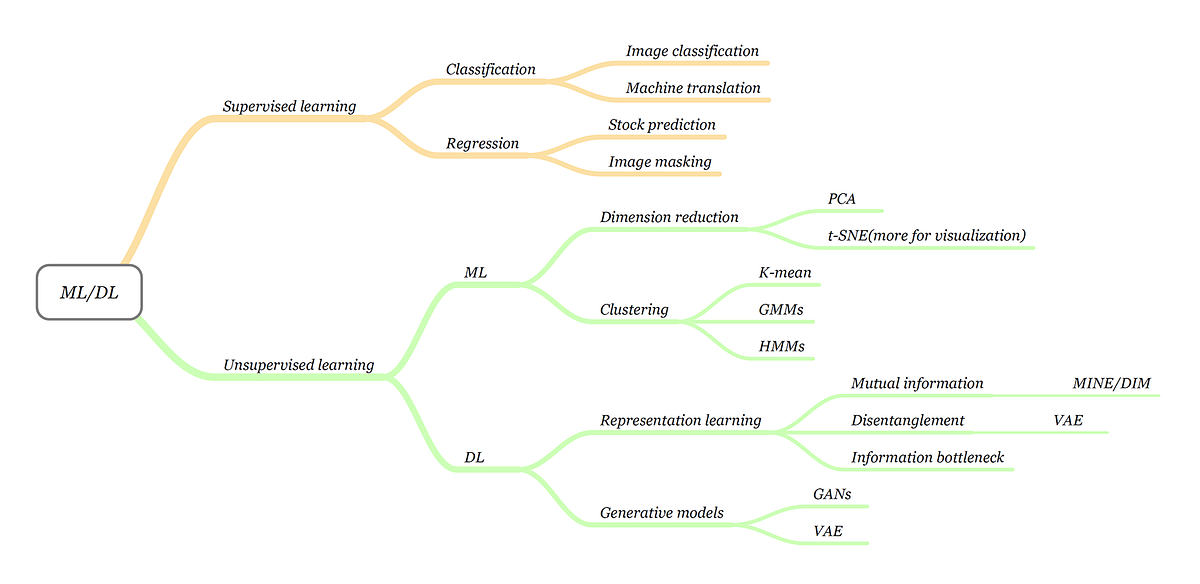
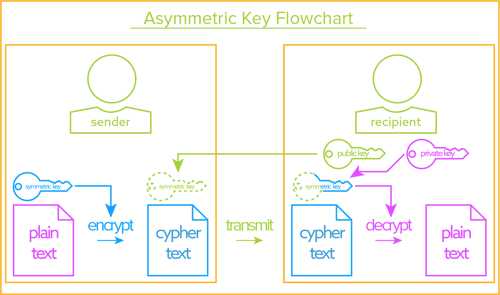
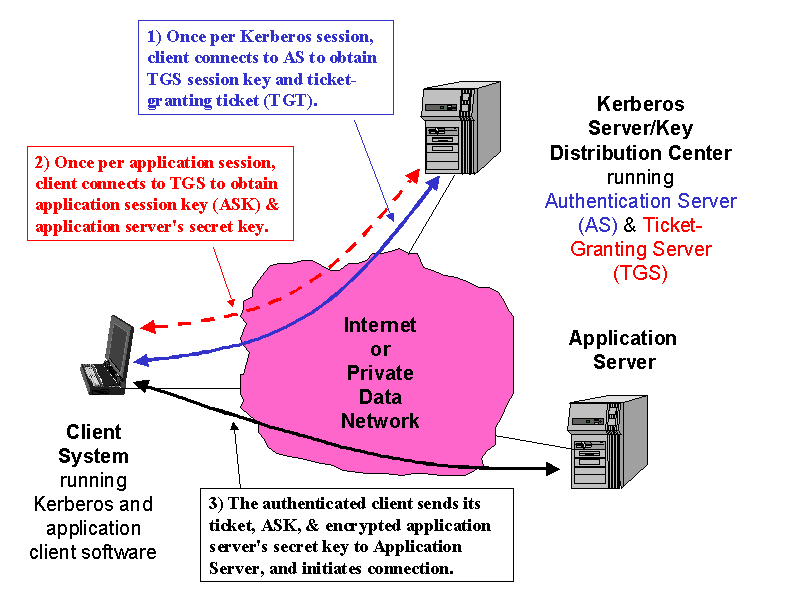
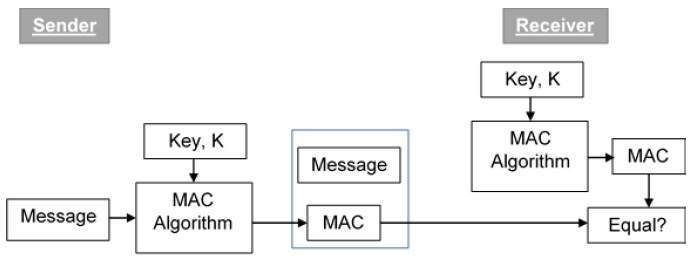
When performing typical public key operations the processor time. In modern cryptography key is a secret known only to or supposed to be the concerned parties the sender and the receiver. The public key is the one used for encrypting to the recipient who can decrypt using his private key. Assymetric encryption algorithms like rsa have one disadvantage.
There are 8 such rounds. All these sub keys will be put on. You sign the key data with a private encryption key and embed the signature in the key and the key validation which implies signature verification among other things is done with a public key. Even though there are dozens of algorithms involved in something like an elliptic curve point addition there are only four algorithms of critical importance.
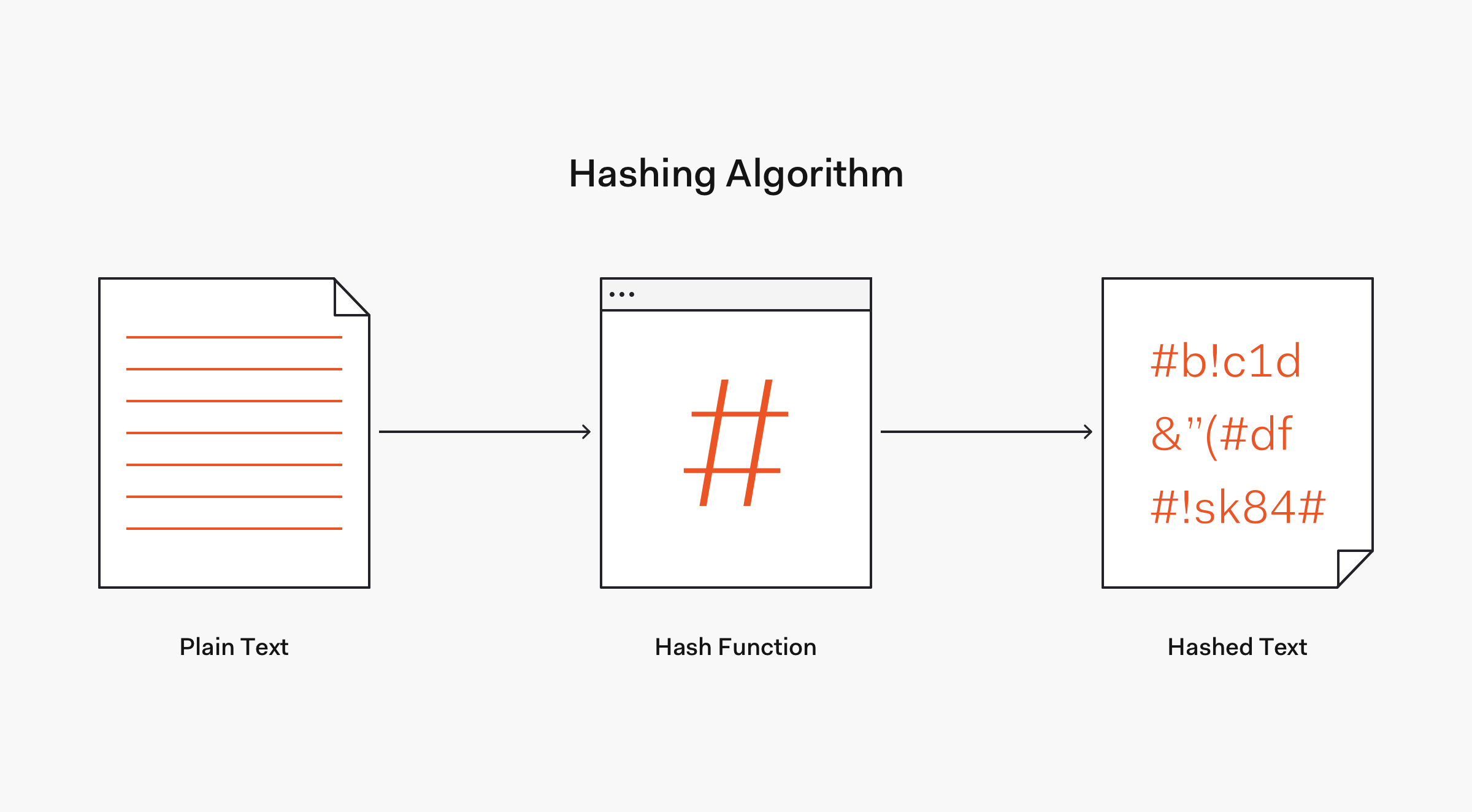
Algorithm is the process used to m. This value is also included in certificates when a public key is used with ecdsa. Here are some crafty tips to help you win if youre the murderous imposter. It is usually a string of 0s and 1s of length dependent on the cipher being used.
Among us pits crewmates against imposters in a mafia like scenario where players dont know who to trust. As a result this robot works under the hood and shows us everything that he thinks we might be interested in. In each round 6 sub keys will be produced.
More From Among Us Key Algorithm
- Among Us Pink Character With Flamingo Hat
- Among Us Mod Antiban
- Can You Get Among Us On Nintendo Switch
- Printable Among Us Mask
- Among Us On Browser
If you are searching for download Among Us On Browser you've reached the perfect location. We have 104 download source about among us on browser including mp3, wallpapers, photographs, backgrounds, and more. In such page, we additionally have number of cheat link out there. Such as png, jpg, animated gifs, pic art, symbol, black and white, transparent, etc.
Incoming Search Terms:
- What Is Encryption And How Does It Work Among Us On Browser,
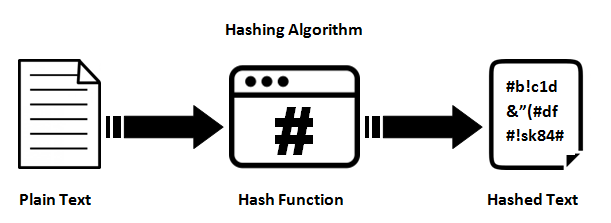
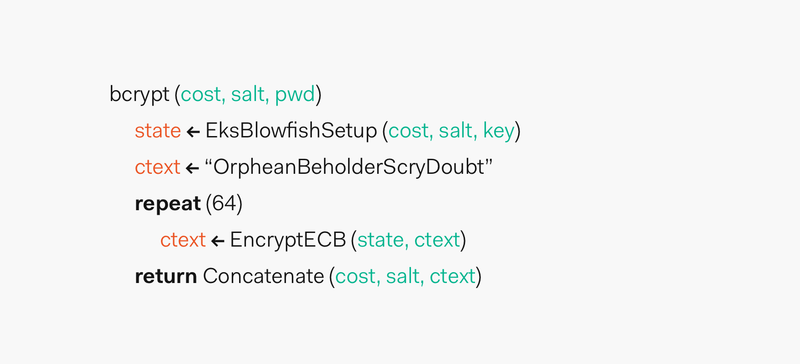
- Types Of Encryption 5 Encryption Algorithms How To Choose The Right One Hashed Out By The Ssl Store Among Us On Browser,
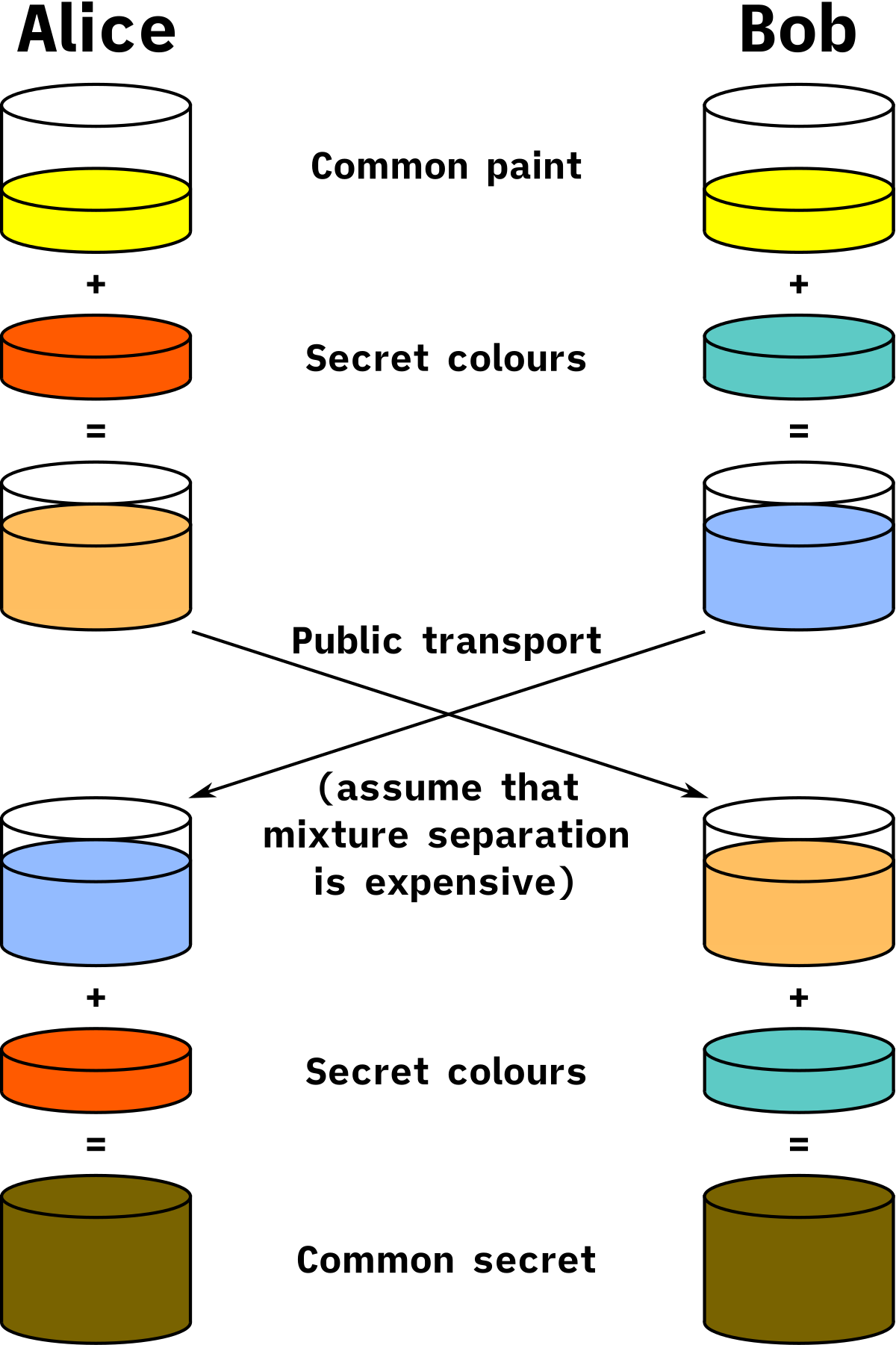
- Diffie Hellman Key Exchange Wikipedia Among Us On Browser,
- Tips For Imposters And Crewmates To Ace In Among Us Essentiallysports Among Us On Browser,
- Algorithm For Post Clustering Curation Of Dna Amplicon Data Yields Reliable Biodiversity Estimates Nature Communications Among Us On Browser,
- Introduction To Digital Signatures And Pkcs 7 Among Us On Browser,





























/cdn.vox-cdn.com/uploads/chorus_image/image/67432589/sc5kzt__1_.0.jpg)