Among Us Keys Algorithm, Common Task Locations And Tips Among Us 1gamerdash
Among us keys algorithm. Among Us Game lately becomes a extremly by famous games, maybe it is because its very addictive game to play. Become an impostor are the dream by every player in Among us keys algorithm game. Because you can kid others and It is funny to see friends fighting each other to vote for the impostor, and sometimes they are of to argue who is Is the true Impostor Among Us Keys Algorithm.
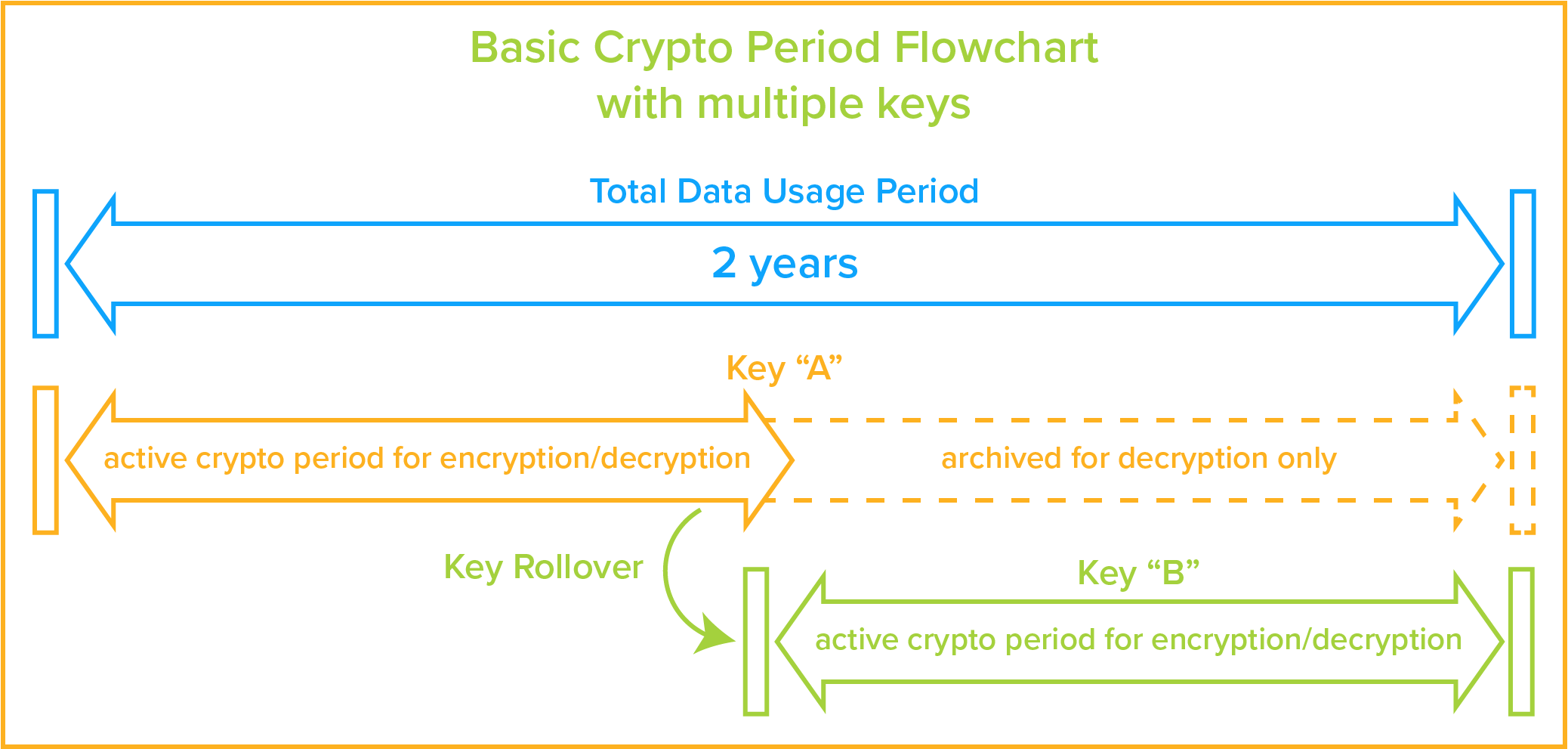
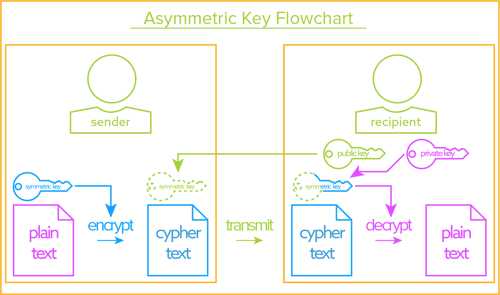
You sign the key data with a private encryption key and embed the signature in the key and the key validation which implies signature verification among other things is done with a public key.

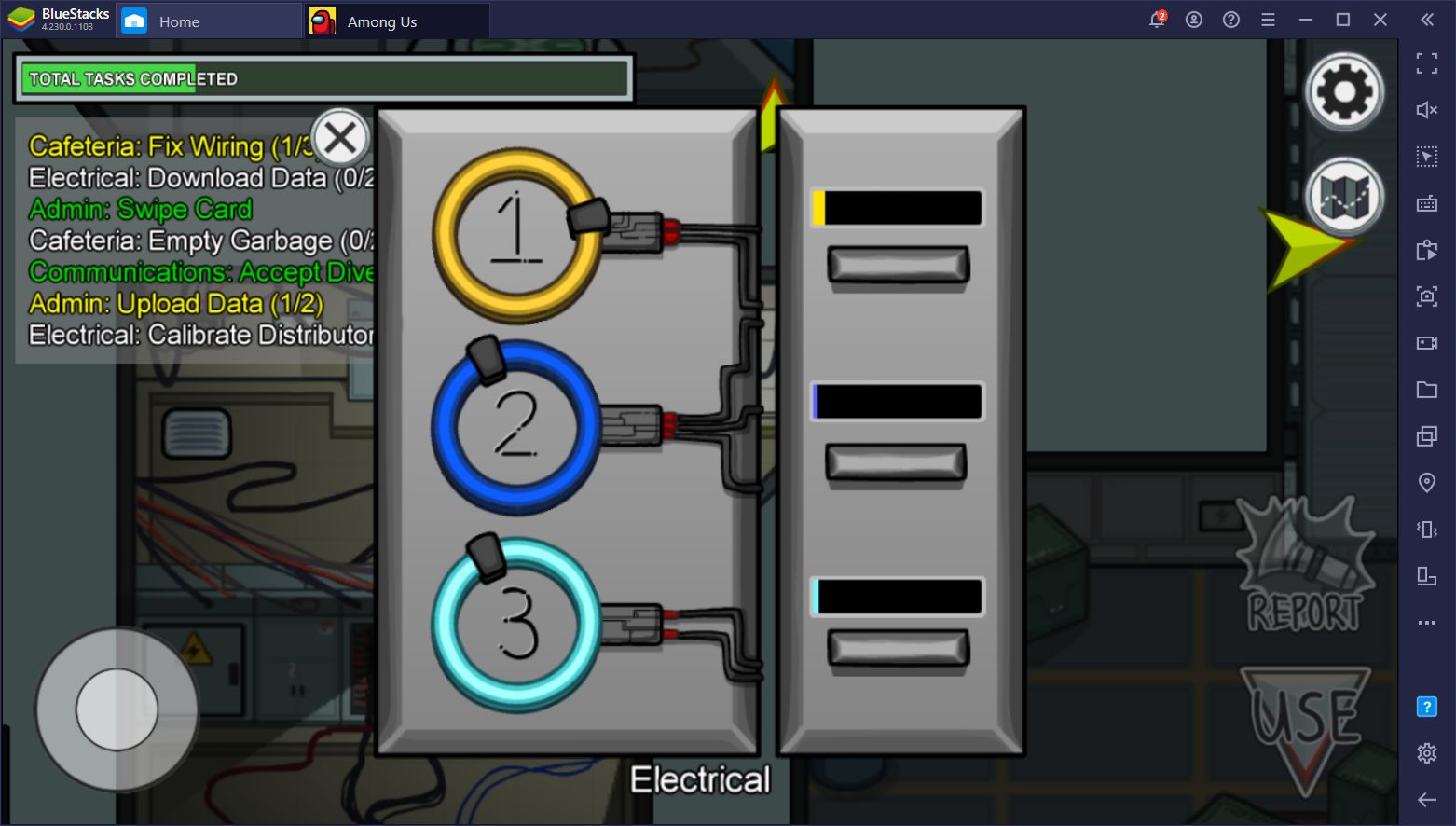
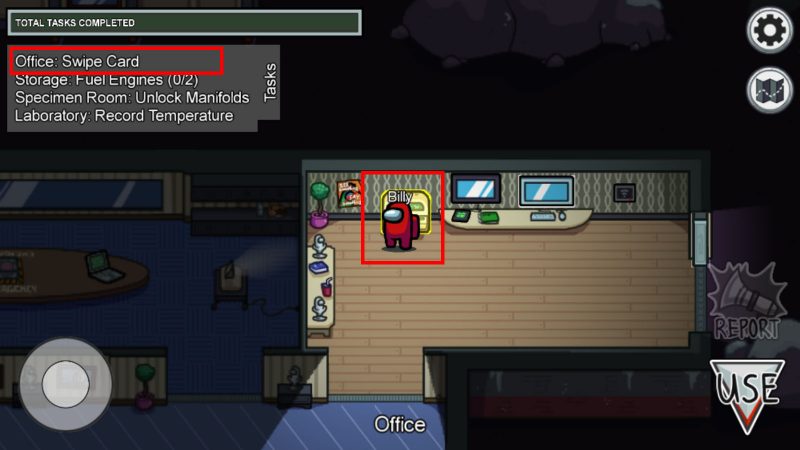
Among us keys algorithm. Multiplication squaring reduction and modular inversion. Here are some crafty tips to help you win if youre the murderous imposter. Among us pits crewmates against imposters in a mafia like scenario where players dont know who to trust. Certain key algorithms when implemented correctly can make a bignum library perform very well.
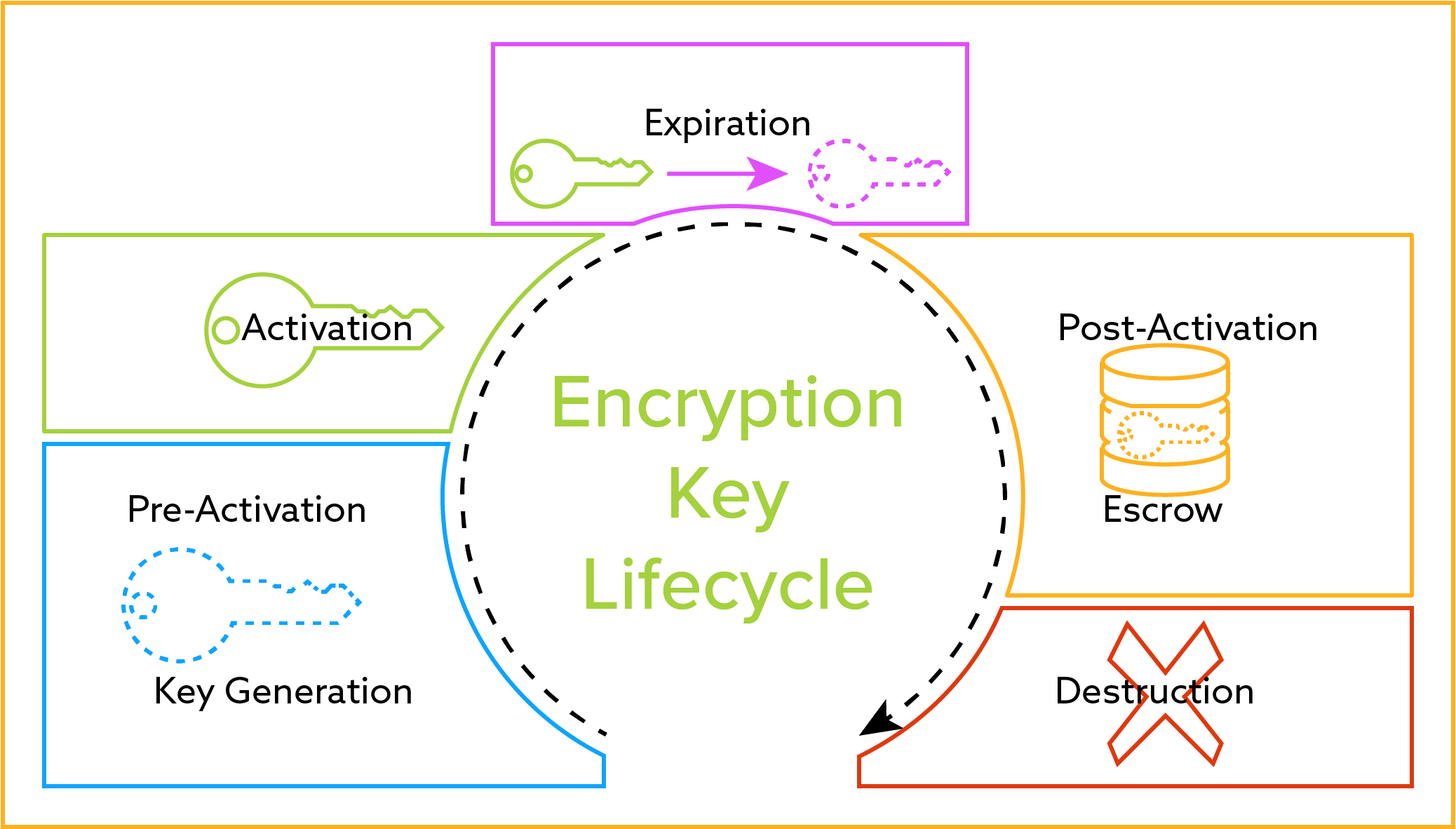
In some cases a physical transfer of the key may be possible and appropriate but more often an electronic means of key delivery is more applicable. Even though there are dozens of algorithms involved in something like an elliptic curve point addition there are only four algorithms of critical importance. Algorithms and key sizes when executing in fips mode system ssl continues to take advantage of the cp assist for cryptographic function cpacf when available. Hardware cryptographic card functions allowed in fips mode support clear keys requires at least one cryptographic card to be defined as an accelerator and online prior to the startup of icsf and secure pkcs 11 keys.
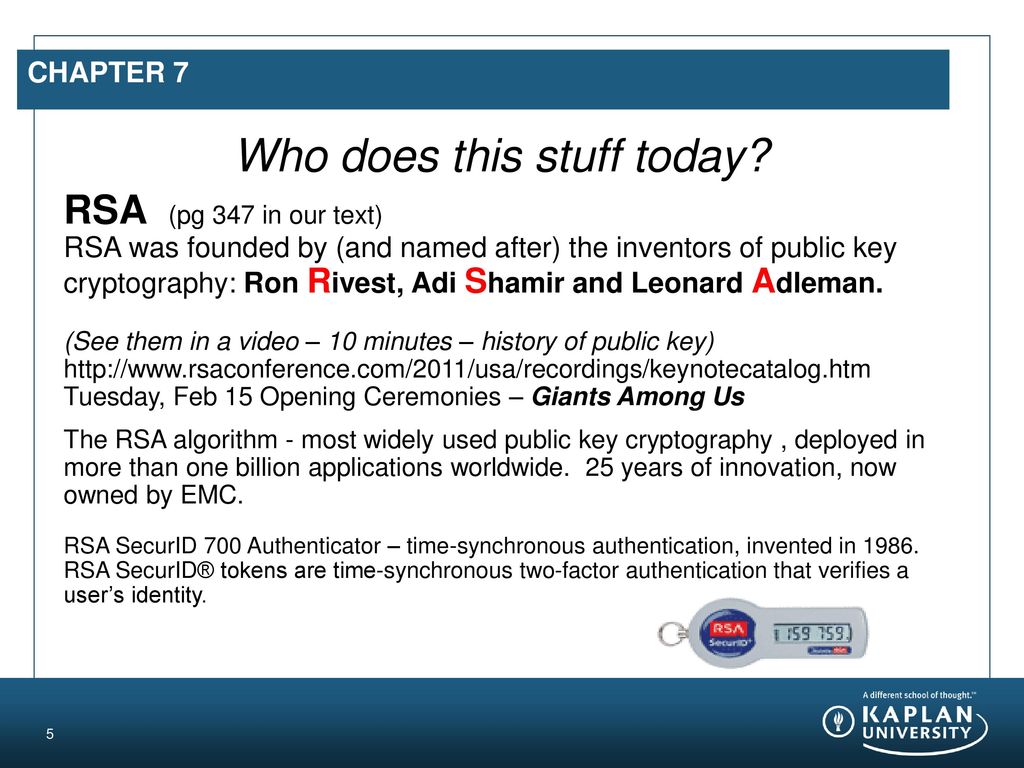
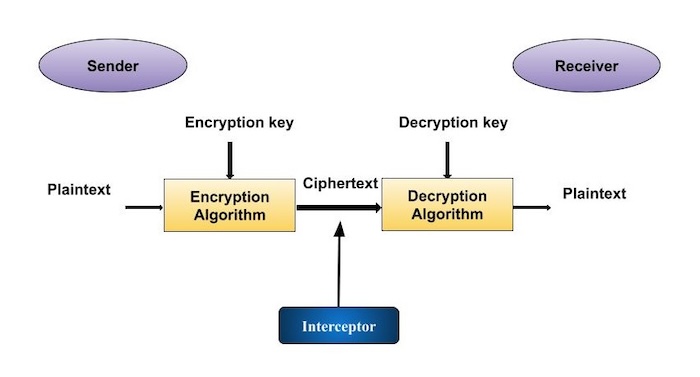
The three algorithms we have looked at so far are all symmetric key algorithms that are very useful if you have a good way to exchange keys with the person or machine with which you want to communicate. However the algorithm allows the private key of one party and the public key of the other party to be combined to produce a resulting key thats the same for both parties. In modern cryptography key is a secret known only to or supposed to be the concerned parties the sender and the receiver. Today in most cases this method is rsa.
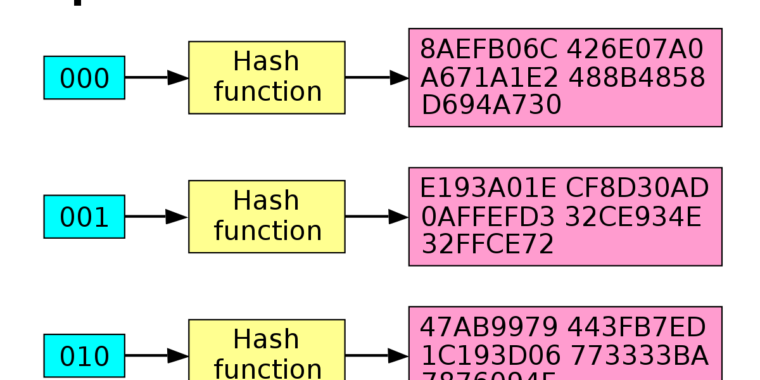
This way no one can create license keys unless they have. When performing typical public key operations the processor time. It is usually a string of 0s and 1s of length dependent on the cipher being used.
More From Among Us Keys Algorithm
- Among Us Orange Transparent
- Among Us Python Bot
- Among Us Anime Maker
- Como Actualizar Among Us En Pc
- Among Us Free Agfy
If you re searching for download Among Us Free Agfy you've arrived at the ideal location. We ve got 104 download links about among us free agfy including apk, wallpapers, photographs, wallpapers, and more. In such web page, we also have variety of cheat link available. Such as png, jpg, animated gifs, pic art, logo, black and white, transparent, etc.
Incoming Search Terms:
- Symmetric Key Encryption An Overview Sciencedirect Topics Among Us Free Agfy,
- Cryptosystems Tutorialspoint Among Us Free Agfy,
- What Is Pgp Encryption And How Does It Work Varonis Among Us Free Agfy,
- A Comparison Of Cryptographic Algorithms Des 3des Aes Rsa And Blowfish For Guessing Attacks Prevention Among Us Free Agfy,
- What Is Asymmetric Encryption Read Symmetric Vs Asymmetric Encryption Diversity Among Us Free Agfy,
- Https Nvlpubs Nist Gov Nistpubs Specialpublications Nist Sp 800 57pt1r4 Pdf Among Us Free Agfy,